Connected To The Leading Players To Drive Automation






Trading Floors Work With
Conversational Data
Increasing workloads and increased competition pressure businesses to improve – to be more responsive, more agile, to improve customer satisfaction, and to cut expenses. However, resources are becoming scarcer as workloads increase.
Customer journeys and business processes rely on conversations – in chats, emails, and oral. Your customer’s needs, products, services, and processes are all gathered in every conversation.
Enhance Customer Experience & Operational Scalability
Make any message actionable. Automate your processes to increase operational scalability and enhance customer satisfaction.
A Cloud Service To
Automate Processes
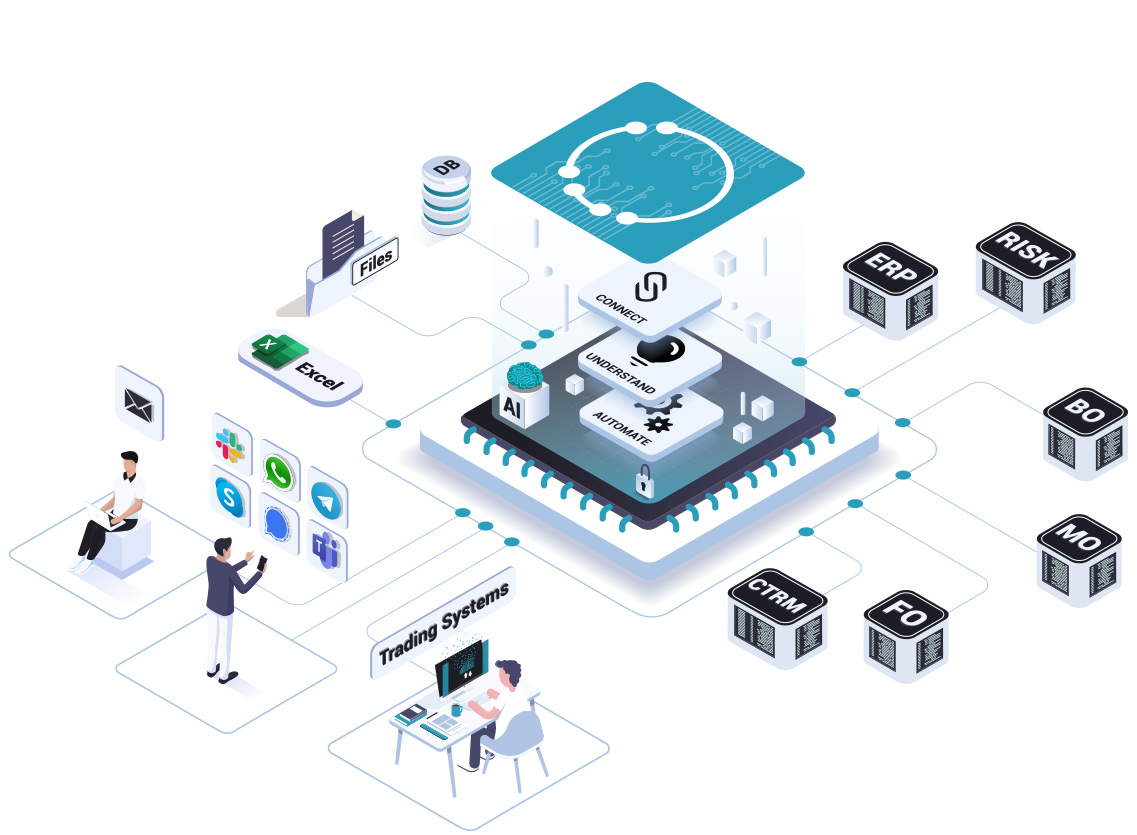
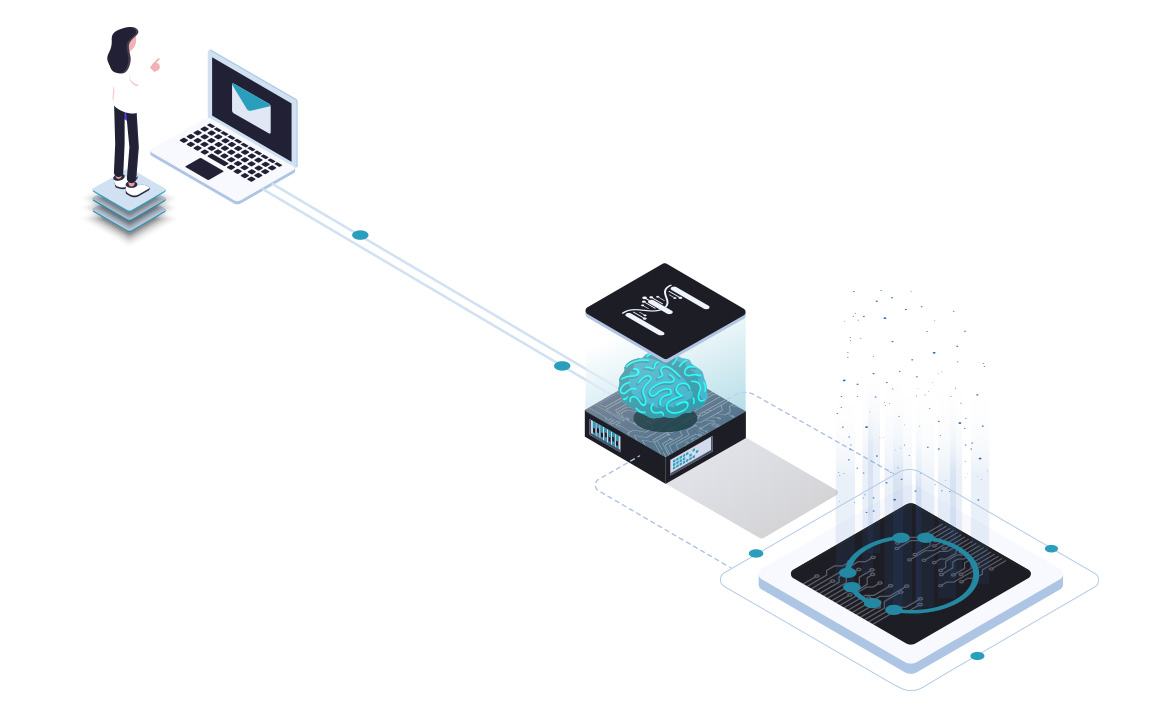
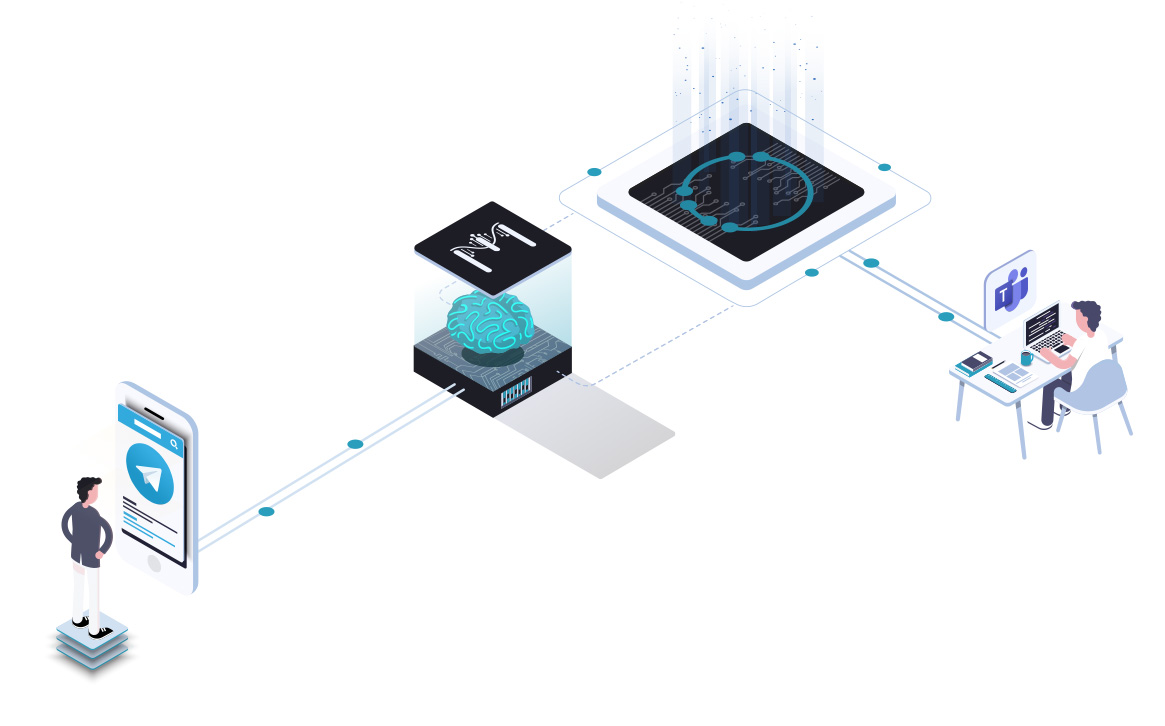
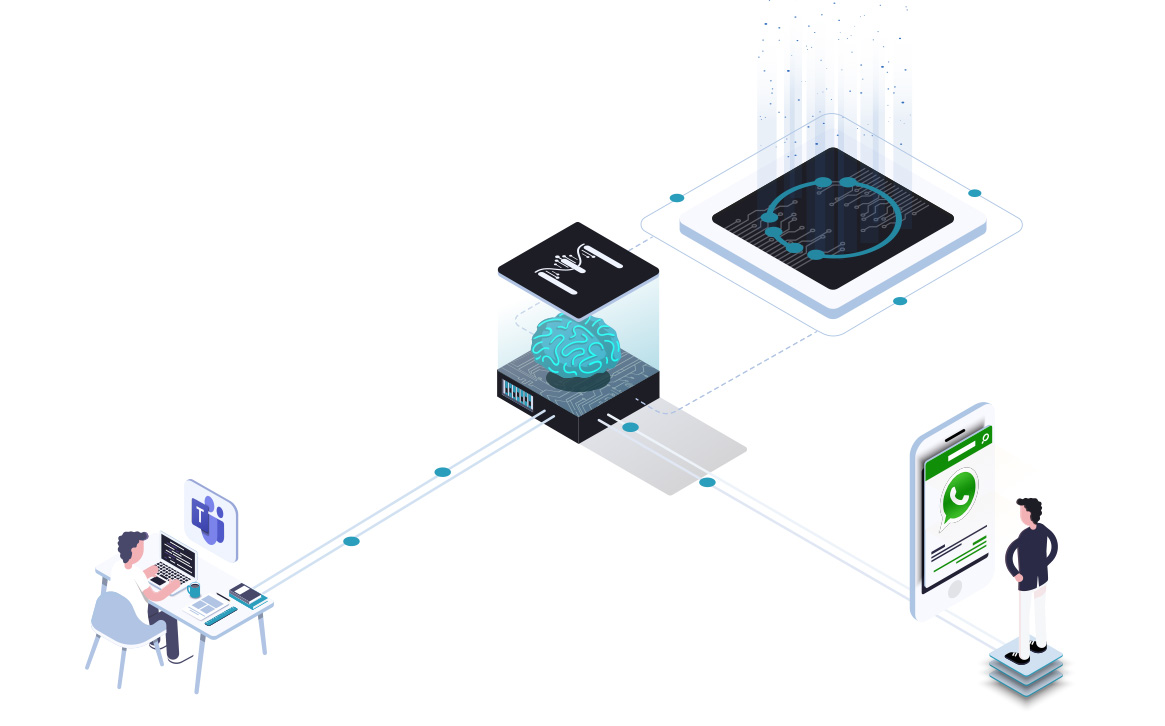
Terranoha Connects to any channel of conversation.
With Terranoha connectors for all channels including email, chat, phone calls, we integrate the structured data into downstream financial applications via our bridges.
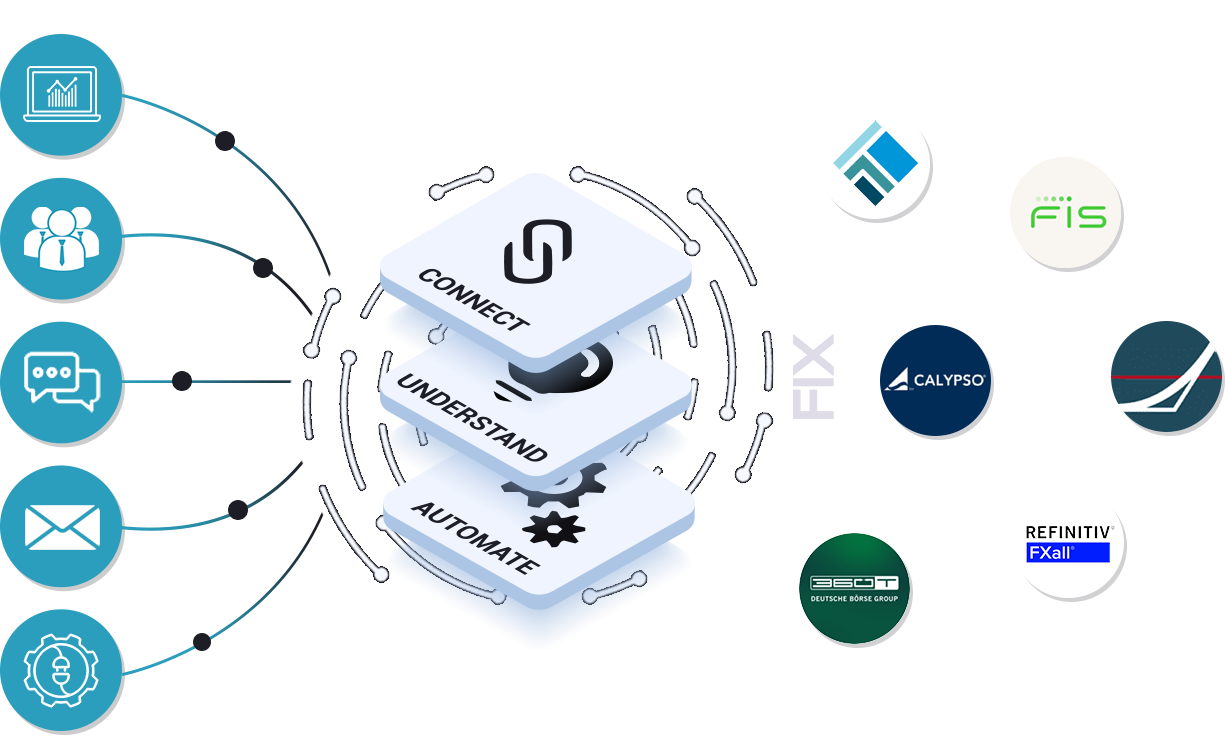
Terranoha solution connects and allows communication between any messaging systems, TMS, OMS, trading systems, brokers.
Terranoha solution understands and harmonizes languages leveraging embedded AI for Natural Language Processing.

RFQ automation Use Cases
Who We Are
Terranoha is a Swiss Fintech founded by financial systems experts with 20+ years of experience. We deliver cloud based financial middleware. We leverage on Artificial Intelligence and Machine Learning to automate all kinds of manual processes within financial institutions.